Stay up to date with the latest news, announcements, and articles.
This article provides a technical examination of what “no verification” actually means in 2025‑2026 markets, how various platforms implement risk‑tiered KYC, and what operational, security, and fraud risks exist when users interact with alternative acquisition channels such as P2P systems, Bitcoin ATMs, or DEX liquidity pools. Instead of promoting unlawful methods, this analysis explores legitimate, compliant methods, clarifies misconceptions, and explains what aspects of the transaction flow are traceable or unverifiable.
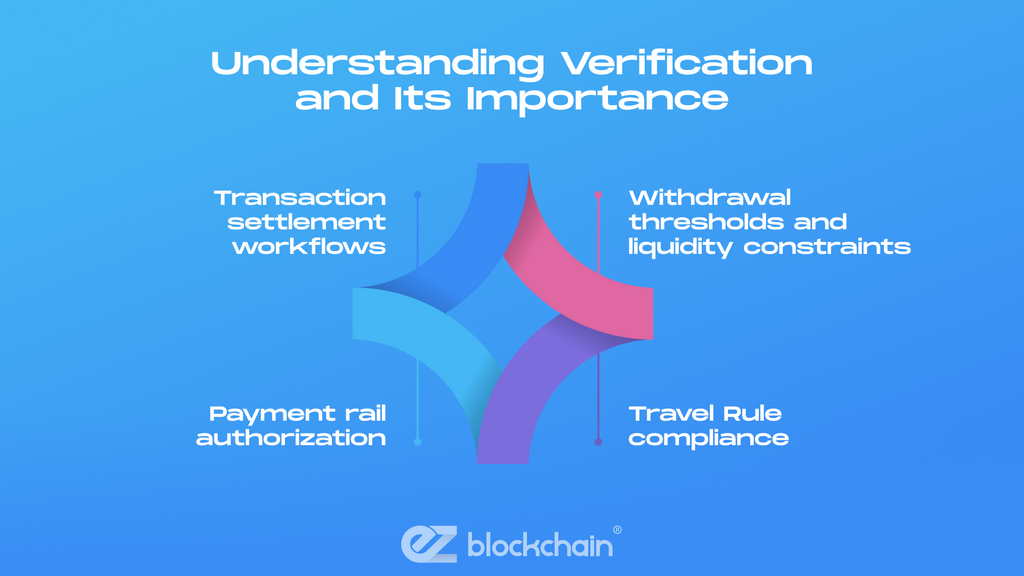
Understanding Verification and Its Importance
Verification (KYC) is not simply an administrative hurdle. It is a core component of financial infrastructure designed to meet AML (Anti‑Money Laundering) and CTF (Counter‑Terrorist Financing) requirements. Regulators such as FinCEN (US), FCA (UK), ESMA (EU), and FATF (global) mandate risk‑based customer due diligence for platforms that qualify as Virtual Asset Service Providers (VASPs).
Technically, verification impacts:
- Transaction settlement workflows (off‑chain → on‑chain transition logic)
- Withdrawal thresholds and liquidity constraints
- Payment rail authorization (ACH, card networks, SEPA, Faster Payments)
- Travel Rule compliance (counterparty data transmission between VASPs)
Even if a user searches for “buy bitcoin no ID” or “bitcoin debit card no verification”, the reality is that regulated institutions cannot execute a transaction without capturing specific customer data once thresholds are met.
Understanding this is essential: the term “no verification” often refers not to complete anonymity, but to low‑tier KYC thresholds, offline acquisition, or decentralized execution without an intermediary.
A nuanced understanding of verification frameworks helps users evaluate where verification is strictly required, where it is risk‑tiered, and where decentralization minimizes the involvement of identity checks, without violating legal or operational standards.
Peer‑to‑Peer (P2P) Platforms
P2P crypto platforms are marketplaces where buyers and sellers transact directly, often supporting cash‑based settlements, digital vouchers, or online payment connectors. Examples include structured platforms (with escrow logic, multi‑sig, or arbitration protocols) and unstructured P2P channels (forums, local meetups, social trading groups).
Technically, modern P2P ecosystems operate on three layers:
- Discovery layer: the listing, matching, and price‑discovery engine
- Escrow/settlement layer: hashed‑time locked contracts (HTLCs), multisig, or custodial escrow
- Reputation and dispute layer: identity verification, trade records, second‑factor dispute metadata
Escrow logic is particularly important. On reputable P2P platforms, a smart contract, federated multisig, or centralized escrow holds Bitcoin until the fiat settlement is confirmed. This prevents double‑spend scenarios and protects both buyer and seller.
Many users assume P2P equals “no verification.” In reality:
- Most platforms enforce identity verification for higher volumes
- AML monitoring flags unusual cash-based or reversible payment methods
- Counterparty risk is high when interacting outside reputable platforms
P2P use cases remain popular, particularly for users researching phrases like “buy bitcoin with gift card no verification” or “buy BTC instantly no verification,” but the modern ecosystem is designed to preserve platform safety rather than avoid oversight.
P2P marketplaces provide flexibility and direct negotiation capabilities, but they rely on robust identity, escrow, and dispute‑resolution systems to maintain integrity. Understanding these technical layers allows buyers to navigate P2P environments safely without assuming the system is inherently anonymous.
Bitcoin ATMs and Local Transactions
Bitcoin ATMs (BTMs) operate as kiosks that convert fiat currency to Bitcoin using on‑chain settlement. They rely on:
- AML-configured hardware modules
- Travel Rule messaging frameworks
- Device-level identity controls (ID scan, phone verification, biometric capture)
- Operator-tier KYC rules
Below is a data table illustrating typical verification thresholds across major US ATM operators (approximate benchmarks based on industry norms):
| ATM Operator Type | No‑Verification Tier | ID‑Required Tier | Additional Requirements |
| Small Local Operators | $20–$300 equivalent | Above $300 | Phone confirmation; sometimes OTC limits |
| Regional ATM Networks | $0–$100 | $100–$2,000 | Government ID; SMS OTP; risk scoring |
| National ATM Chains | None; ID always required | $1,000+ | KYC; biometric scan; address verification |
Technical reality: While many online queries imply “no verification,” the majority of US‑based ATMs require ID starting at low thresholds. This shift is driven by regulatory enforcement, increased Travel Rule adoption, and fines issued between 2021–2024 to non‑compliant operators.
Local cash transactions (in-person trades) can occur outside formal KYC infrastructures, but they carry high counterparty risk, and security considerations (personal safety, counterfeit cash, coerced transactions) outweigh convenience.
Bitcoin ATMs remain a popular acquisition method for low-volume, convenience-driven purchases, but modern AML standards mean that true “no verification” tiers are limited, tightly capped, or fully removed depending on the operator’s risk model and jurisdiction.
Decentralized Exchanges (DEX) Options
DEXs, like Uniswap, Bisq, Phoenix, or other non-custodial trading protocols, use smart contracts rather than centralized order books. They allow users to swap assets using:
- AMM (Automated Market Maker) liquidity pools
- Liquidity provider (LP) bonding curves
- HTLC cross-chain swap logic
- P2P decentralized order matching
Because DEXs never take custody of user funds, they typically do not conduct KYC. The user trades directly from a self‑custodial wallet, interacting with smart contracts on-chain.
However:
- Buying Bitcoin directly on a DEX is limited by network support (e.g., BTC/ETH cross-chain bridges)
- Users still need funding rails to obtain the initial crypto used for swapping
- Many DEX‑Bitcoin solutions rely on wrapped or synthetic Bitcoin (e.g., WBTC, tBTC, renBTC)
For users searching “buy bitcoin no verification”, DEXs offer non-custodial execution, but not fiat onboarding. Fiat conversion always touches regulated infrastructure.
DEXs provide privacy‑preserving execution and avoid custodial risks, but they do not bypass fiat‑to‑crypto KYC requirements. They excel at swaps, not fiat onboarding, and understanding this distinction is key for realistic expectations.
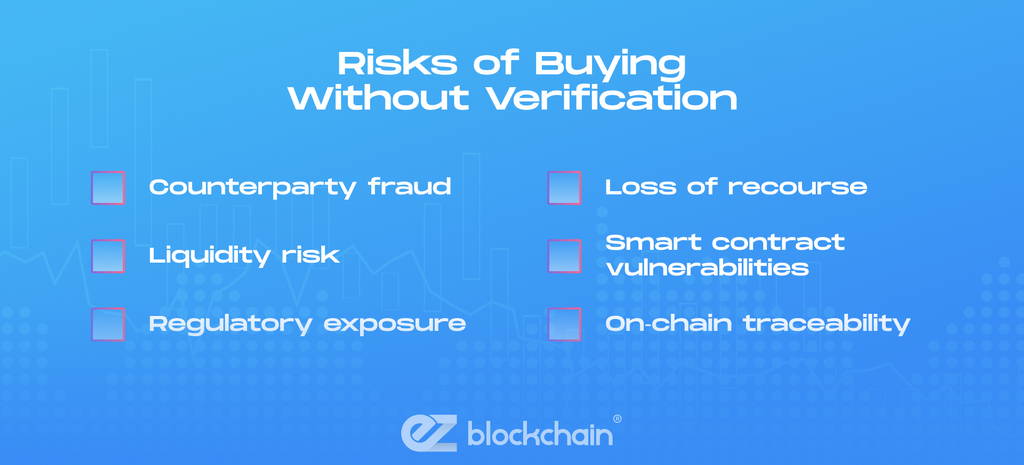
Risks of Buying Without Verification
Operating in low‑verification environments introduces substantial risks. These include:
- Counterparty fraud (fake receipts, chargebacks, impersonation, counterfeit bills)
- Liquidity risk (poor pricing, thin order books, unfavorable slippage)
- Regulatory exposure (transactions flagged due to proximity to illicit flows)
- Loss of recourse (no support tickets, no dispute resolution)
- Smart contract vulnerabilities (for DEX‑based or escrow‑based flows)
- On‑chain traceability (lack of privacy if address hygiene is poor)
A buyer focused solely on “no verification” channels increases exposure to operational and financial instability.
Risk compounds significantly in unverified environments. Understanding these dimensions allows users to choose platforms that balance privacy with security, liquidity, and legal compliance.
Avoiding Scams and Fraud
Fraud vectors are widely documented in P2P and ATM ecosystems. Common threats include:
- Reversible payment methods used maliciously
- Impersonation schemes in messaging apps
- Fake escrow platforms that mimic reputable ones
- QR code manipulation
- Address poisoning attacks
Technically sophisticated scams now use deepfake voice calls, synthetic KYC files, and transaction replay phishing. Awareness is the primary defense.
Fraud in alternative acquisition channels evolves rapidly, combining social engineering with technical deception. Maintaining operational hygiene, verifying counterparties, and using escrow smart contracts when possible provides meaningful protection.
Limits and Restrictions to Consider
Even where low‑verification tiers exist, users encounter constraints:
- Low maximum thresholds per transaction
- Daily or monthly limits
- Premium fees (10–20% at some ATMs or P2P trades)
- Restricted payment rails (prepaid cards, ACH, gift cards)
- Geofencing and IP-based blocking
- Unavailability during heightened AML enforcement cycles
These limitations are structural and designed to comply with AML guidelines.
Purchasing Bitcoin with minimal verification is restricted by design. Operational, logistical, and regulatory controls define the boundaries within which such transactions can occur.
Securing Your Bitcoin After Purchase
Security becomes even more relevant when using less regulated rails.
Key technical recommendations include:
- Use hardware wallets with secure enclaves and deterministic key generation (BIP32/39/44)
- Enable multi‑sig configurations (2-of-3 models via Specter or Sparrow)
- Rotate addresses per transaction to avoid clustering heuristics
- Avoid leaving coins in temporary custodial wallets after P2P or ATM purchases
- Use coin control features to minimize UTXO trace linkage
Post‑purchase security is non‑negotiable. Proper custody, address hygiene, and UTXO management protect users from traceability risks and unauthorized access.
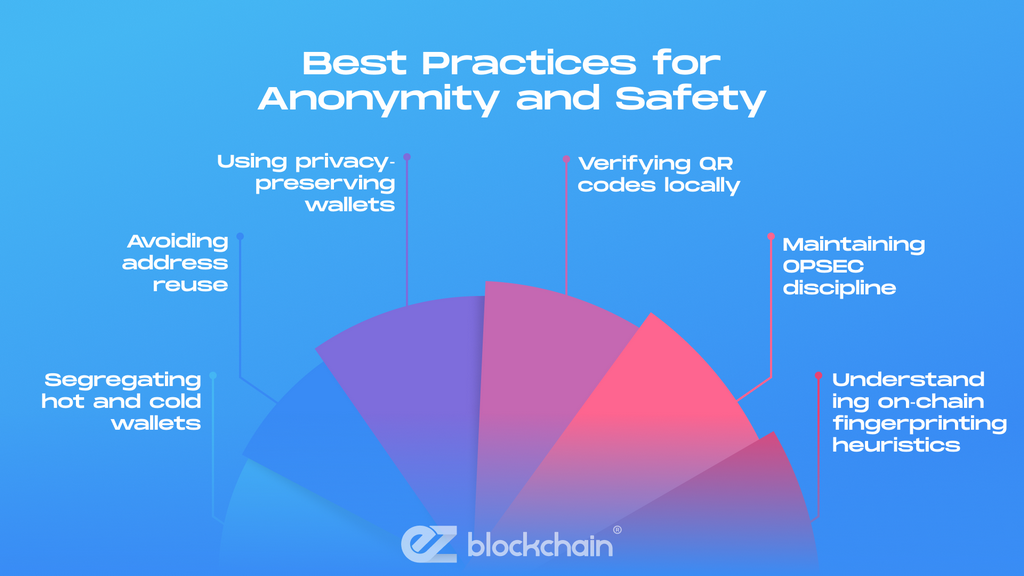
Best Practices for Anonymity and Safety
While anonymity cannot override legal frameworks, users can enhance privacy responsibly. Best practices include:
- Segregating hot and cold wallets
- Avoiding address reuse
- Using privacy‑preserving wallets (CoinJoin‑compatible, Tor‑enabled)
- Verifying QR codes locally
- Maintaining OPSEC discipline (no screenshots, no shared addresses)
- Understanding on‑chain fingerprinting heuristics
These practices enhance privacy without violating laws.
Responsible anonymity focuses on protecting user data, not circumventing regulations. Technical discipline, custody best practices, and privacy‑preserving tooling provide meaningful protection while staying compliant.
Final Thoughts
The phrase “buy Bitcoin with no verification” is often misunderstood. In practice, modern crypto infrastructure, P2P, ATMs, and DEXs, operates within a complex regulatory matrix. True anonymity is rare, low‑volume, heavily limited, or technically impractical. What users can achieve, however, is legitimate, compliant, privacy‑conscious acquisition of Bitcoin supported by strong security, decentralized execution, and responsible operational practices.
Fill out a form and our bitcoin mining expert will contact you.
FREE CONSULTATIONchoose
a miner
profit and
understand data?
business remotely
with EZ Blockchain?
Fill out a form and our bitcoin mining expert will contact you.